Employee Monitoring Made Simple
Record, Review, Alert and Block User Activity
Easy-to-Use and Install. Start Today.
Monitor All Devices from One Interface
Get the control and oversight that's right for you.
Which use case best describes your goals?
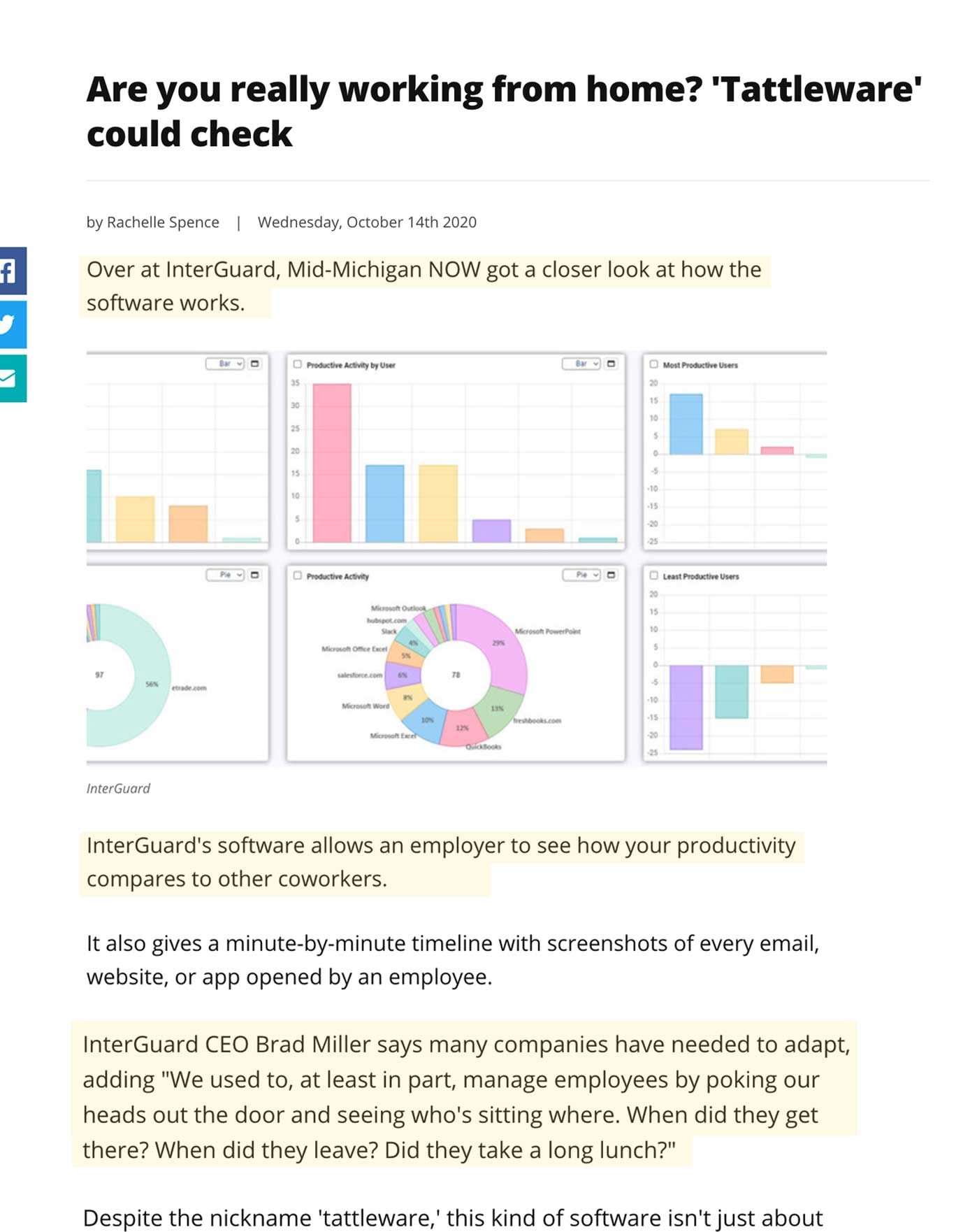
Employee Productivity Monitoring
InterGuard Employee Monitoring software lets you record and track all your employee’s productivity – so you’ll know if they are working hard or hardly working.
- Monitor Computer Activity
Watch as work unfolds in real time with desktop screenshots & video playback. - Measure Productivity & Idle Time
Get reports and alerts about how employees use their time, app and website usage. - Manage Remote Workers
Monitor remote workers to ensure they stay on task. Trust, but verify.
Protect against Insider Threats
Knowing who is accessing sensitive files or participating in risky activities, is good but it’s not enough. Preemptively block unwanted behaviors, and react in real-time to alerts.
- Data Loss Prevention
Restrict access to high-risk programs, websites, USB storage, and email attachments. - Risky Keyword & UAM Alerts
Get alerted to suspicious activities whether triggered by keywords, policy violation attempt or anomalous behaviors. - Remote Incident Response
Retrieve sensitive files, delete stolen assets or lock devices down completely.
Investigations & Compliance Audits
Whether proving regulatory compliance, conducting HR investigations or tracking down a suspected internal data breach, InterGuard presents user activity data in a clear, easy-to-understand format.
- Internal Investigations
Get the proof you need to respond to complaints of discrimination, wrongful termination, and sexual harassment quickly. - Satisfy the Auditor
If you need to comply with regulations (e.g. HIPAA, PCI, CIPA), InterGuard collects the raw data you need, then lets you create detailed, meaningful reports. - Session Recordings and Screenshots
Get the context you need by viewing the screenshots of suspicious activities carried out on the employee's desktop
With an improved user interface and a gamut of employee productivity monitoring features, InterGuard converts data into useful insights and has a host of proactive alerts for larger businesses, especially those now focused on managing a remote workforce.

The Best Employee Monitoring Software Makes Insight Easy



Monitor Multiple Employees in a Single Dashboard
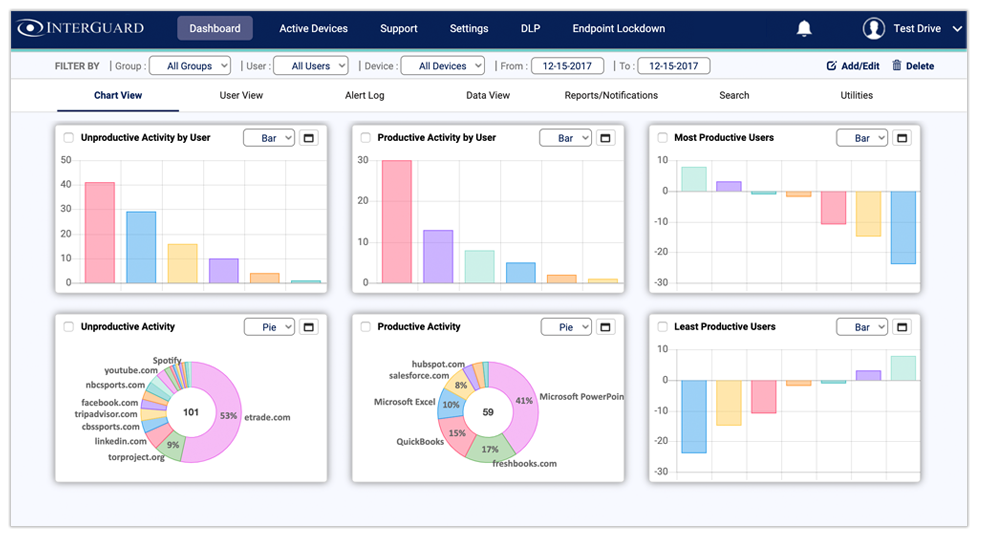
User and Entity Behavior Analytics
Create a benchmark of acceptable activity and get notified when any user exceeds or does not reach your selected benchmark.
Endpoint Lockdown
Interact with and take control of a user's PC/laptop in a potential breach situation. Remotely delete or retrieve files, or lockdown the endpoint if necessary.
Employee Monitoring FAQ's
How do I monitor user activity?
User activity monitoring software uses the several criteria to track, record, log, analyze and alert all actions made on company devices,Keylogging and keystroke monitoring, screenshots, User Behavior Analytics, file tracking
Email and chat monitoring, and web and program monitoring. The
benefits of monitoring software far outweigh the potential disadvantages. If you aren’t already using user activity monitoring software, check out these top reasons why you should.
How does laptop tracking software work?
Laptop tracking software encompasses broad-reaching capabilities for companies that need assurance that employees meet productivity standards, comply with corporate policies and adhere to safe and appropriate online behaviors. Monitoring creates data footprints that can provide the support companies need to counter legal disputes, decrease time theft and to support raises and promotions for employees who have clearly excelled in their positions. Let InterGuard work to keep your company protected from internal and external threats and help managers uncover employees who are going above and beyond their job duties (and those who are not).
How to block employees from accessing websites?
Each organization is different, and each needs its own unique website filtering arrangement. InterGuard is flexible and allows for individualization. You can filter by URL, by category, by keyword or by all three. Make sure your employees maintain a safe and proper balance between work-related online activities and time-wasting web surfing with InterGuard's web filtering and website blocking.
Does employee monitoring increases productivity?
Using
employee productivity tracking can help improve productivity in your workplace and protect your company’s bottom line. But like any tool, employee productivity tracking can be used correctly or it can be used in a way that causes more problems than it solves. In order to get the maximum benefit from employee productivity tracking, you need to know how to use it correctly.
Take a look at what you need to know in order to get the best possible results from the moment you start tracking your employees productivity.
How do you monitor employee performance?
All companies are looking for ways to drive higher performance, productivity and profits, but without any data to affect change is only going to have a minimal impact. Employee performance can be measured in many ways, but one of the most important indicators is how employees manage their daily activities at the endpoint. This can be achieved with user behavior analytics coupled with computer monitoring. Click here to learn more about how InterGuard can increase employee performance with User Behavior Analytics.
How do I track employee computer activity?
With the remote workforce now going mainstream, though, monitoring computer activity might be the only solution to maintain accountability and keep managers aware of how company time is spent from those virtual workspaces.
Installing InterGuard's remote computer monitoring software is the best way to keep track of what your employees are doing on their devices. Our software is easy to install and can track digital activity for both employees who are in the office and employees who work remotely.
Employee Monitoring Software that Gives You More
InterGuard is the easiest and fastest way for you to monitor, control and respond to what employees do on their computers and phones